In today’s interconnected world, the digital age seamlessly intertwines with our everyday lives and information flows freely. Inside the work area, Virtual Assistants play a vital role to maintain a Client’s online security and privacy. As we share our thoughts, and connect with others across other digital channels, the need to protect our personal information is an utmost priority. This is where the importance of a Virtual Assistant comes into play.
Ever wondered how hackers pull off their digital trespasses? Are you curious about who might be peeking over your virtual shoulder to catch a glimpse of your Client’s information? Well, you’re not alone! In this generation of fast-paced digital advancement, the internet has completely changed; how we communicate, work, and deep dive into the complete area of human knowledge.
We’re here to clarify the challenges of Technical jargon and offer practical tips for your digital life. As the saying goes, “With great power comes great responsibility.” – The responsibility to protect sensitive data from the prying eyes of Cybercriminals.
At the heart of this effort are our Virtual Assistants (VAs). Just as you’d lock your front door to keep your home secure, our VAs act as digital Partners. They navigate the twists and turns of your digital environments. VAs are not only responsible to manage and ease Clients’ tasks but are also entrusted with sensitive data. Whether you manage a Law Firm or a Business Owner, VAs can help you understand the challenges of online security and privacy.
Together, we’ll ensure that every click you make is a step towards a safer and more confident digital you!
 1. The role of a Virtual Assistant goes beyond mere task execution. This also includes the need to protect the Client’s sensitive data that could harm them if it fell into the wrong hands.
1. The role of a Virtual Assistant goes beyond mere task execution. This also includes the need to protect the Client’s sensitive data that could harm them if it fell into the wrong hands.
2. Virtual Assistants take responsibility while safely handling their Client’s data. This involves a safe transfer of information with security code and secure communication tools as needed. Additionally, they refrain from keeping sensitive information beyond its required period. They also ensure that any stored data is properly protected against unauthorized users.
3. Virtual Assistants provide strong control measures to ensure that only authorized individuals can access the Client’s information. These measures include the use of strong Passwords, Multi-Factor Authentication, and restricted access to those with a real need-to-know.
4. When VAs exchange sensitive information or discuss confidential matters, they opt for secure communication channels. This includes using encrypted email or communication apps to prevent interception by malicious actors. Furthermore, they remain vigilant against malicious emails, links, or attachments in any case of potential security risk.
5. While sharing files with other Clients or team members, Virtual Assistants opt for secure file-sharing methods. VAs also use strong Passwords and enable device encryption as an added layer of protection. This is to keep the file inaccessible to unauthorized users and to ensure increased security.
1. Non-Disclosure Agreement –  This Non-Disclosure Agreement, also known as an “NDA,” is a legal contract between the Virtual Assistant and the Client. This outlines the terms and conditions required to handle and protect sensitive information. Therefore, NDAs must be carefully drafted to ensure they are legally enforceable and within in the guidelines.
This Non-Disclosure Agreement, also known as an “NDA,” is a legal contract between the Virtual Assistant and the Client. This outlines the terms and conditions required to handle and protect sensitive information. Therefore, NDAs must be carefully drafted to ensure they are legally enforceable and within in the guidelines.
Furthermore, an NDA indicates not only the commitment of both parties but also maintains confidentiality for your business. This builds trust between the Virtual Assistant and the Client, creating a more positive and effective working relationship.
2. Time Tracking – This is a valuable practice that benefits both the Virtual Assistant and the Client for improved productivity and professionalism. Using time-tracking software such as Hubstaff monitors the time your Virtual Assistant spends on various tasks. This not only helps in tracking efficiency but also ensures that VA stays focused on work-related tasks during the agreed hours.
Additionally, time-tracking allows correct billing for both the Virtual Assistant and the Client. Therefore, clears up any misunderstandings and disagreements about billing. Similarly, time-tracking helps Clients to better manage their budgets. They can keep track of how much is being spent on various tasks and adjust their budget accordingly.
 Monitoring and tracking tools seamlessly add a layer of supervision and boost responsibility in the Virtual Assistant-Client relationship. Likewise, they play an important role in keeping data private and rule adherence. While monitoring should be done with respect to legal boundaries, it can help ensure that the VA adheres to security protocols. Consider using task management tools such as Filevine, Trello, Asana, or Monday.com to assign tasks and projects.
Monitoring and tracking tools seamlessly add a layer of supervision and boost responsibility in the Virtual Assistant-Client relationship. Likewise, they play an important role in keeping data private and rule adherence. While monitoring should be done with respect to legal boundaries, it can help ensure that the VA adheres to security protocols. Consider using task management tools such as Filevine, Trello, Asana, or Monday.com to assign tasks and projects.
Additionally, these tools help quickly and effectively address security incidents. Generally, they foster better communication, smoother teamwork, and increased effectiveness in both task management and security maintenance.
4. Data Access Control – By using strong Data Access Control measures, Virtual Assistants can regularly manage access to sensitive information. Simultaneously, this allows the VA to control who sees the data and keeps the Client’s information private. Having this ability not only creates strong security but also reduces the risk of data leaks, which significantly improves responsibility. Keeping a strong sense of responsibility builds a safe and transparent environment. Therefore, Clients can feel confident that their private information is secure.
This is a summary the Virtual Assistant provides to the Client at the close of each working day. In addition, this report aims to provide a clear summary of the tasks, and activities completed throughout the day. Generating End-of-Day reports is certainly a testament to the Virtual Assistant’s dedication and commitment. This transparent approach coupled with reports that show progress in real-time gives Clients a clear understanding of ongoing efforts.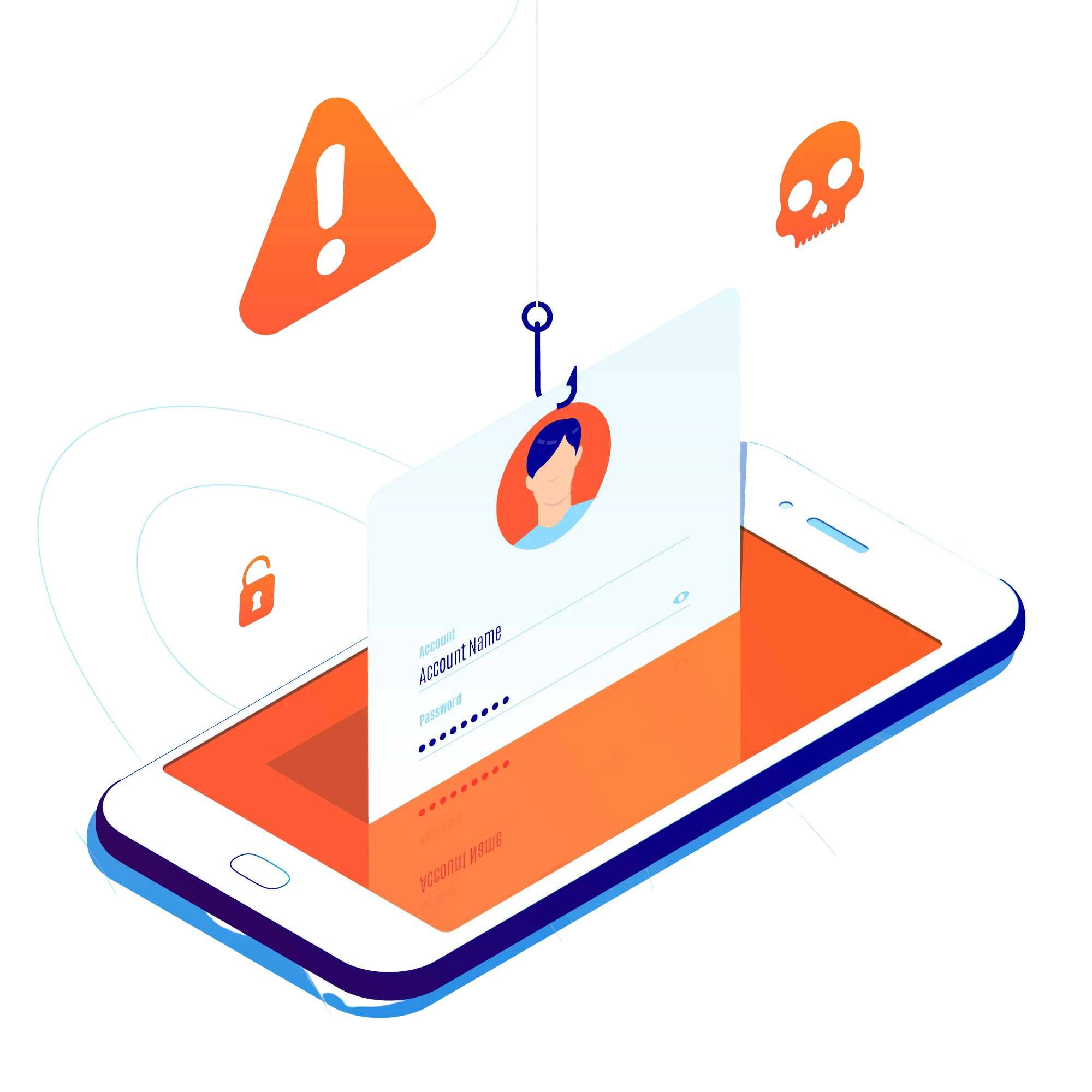
Ultimately, these reports offer immediate transparency and accountability which are fundamental pillars of successful working relationships. The End-of-Day Report serves as a beacon of proactive measures.
6. Secure Communication Channels – Having secure communication channels is equally important in a VA’s role towards their Client’s online security and privacy. Firstly, these secure communication channels lay the groundwork for trust between the Virtual Assistant and their Client. Not only will it guarantee the Client’s security, but also indicates the VA’s commitment to protect their Clients’ confidential data.
Secondly, secure communication channels are crucial to protect sensitive information from cyber threats. Therefore, using encrypted and protected communication prevents unauthorized individuals from getting data and keeps it safe from malicious actors.
Lastly, Virtual Assistants must adhere to various data protection rules and privacy standards. This includes the General Data Protection Regulation, the Health Insurance Portability and Accountability Act of 1996, and the California Consumer Privacy Act.
 Virtual Assistants perform regular audits to ensure online security and privacy for Clients. Through these audits, they not only identify weak points but also ensure they’re following the rules. Consequently, it allows them to detect unusual activities, adapt to threats, and make the whole system better.
Virtual Assistants perform regular audits to ensure online security and privacy for Clients. Through these audits, they not only identify weak points but also ensure they’re following the rules. Consequently, it allows them to detect unusual activities, adapt to threats, and make the whole system better.
The backbone of a Virtual Assistant’s efforts lies in these audits. Thus, ultimately leads to creating a safer online environment for the Client’s business and its stakeholders. Additionally, Clients place their trust in Virtual Assistants who prioritize security and conduct thorough audits to safeguard their business reputation. This practice not only establishes trust but also enhances the Virtual Assistants’ skills and nurtures robust Client relationships.
Concurrently, audits conducted for Clients result in a more secure digital environment, guarantee legal adherence, instill trust, and improve efficiency. This approach to mutual benefit promotes teamwork that is team-oriented and secure.
 While having secure file-sharing is crucial, A Virtual Assistant must also prioritize using a Password Manager. These extra measures protect a Client’s information and prevent security breaches. Adding an extra layer of security involves turning on two-factor authentication or multi-factor authentication.
While having secure file-sharing is crucial, A Virtual Assistant must also prioritize using a Password Manager. These extra measures protect a Client’s information and prevent security breaches. Adding an extra layer of security involves turning on two-factor authentication or multi-factor authentication.
Further, as part of a Virtual Assistant’s responsibilities, it is important to choose a reputable file-sharing platform with strong encryption. For instance, tools such as Dropbox Business, Google Workspace, and Microsoft OneDrive for Business, are notable tools in this regard.
Tools such as VeraCrypt or built-in encryption ensure intercepted files remain unreadable unless a decryption key is available. Furthermore, configuring access permission to limit the download of shared files significantly enhances the security of the Clients’ data. Finally, it’s vital to regularly update the file-sharing platform and relevant software with the latest security updates to protect against known vulnerabilities.
 Besides the realm of online security and privacy, the role of a Virtual Assistant goes far beyond Administrative tasks. VAs must be aware of all potential risks, such as phishing attacks, malware, and data breaches. Moreover, since VAs often access sensitive data such as personal, financial, and business-related information, proper training plays a vital role. Similarly, they can effectively recognize and indeed respond to threats, thereby reducing the likelihood of security incidents that could harm both the VA and the Client.
Besides the realm of online security and privacy, the role of a Virtual Assistant goes far beyond Administrative tasks. VAs must be aware of all potential risks, such as phishing attacks, malware, and data breaches. Moreover, since VAs often access sensitive data such as personal, financial, and business-related information, proper training plays a vital role. Similarly, they can effectively recognize and indeed respond to threats, thereby reducing the likelihood of security incidents that could harm both the VA and the Client.
Ample training and heightened awareness of a VA’s responsibilities are a pivotal part of their role in your business. This includes knowing best practices for online security, such as using strong, unique Passwords, enabling two-factor authentication, and up-to-date software. This approach not only safeguards the Client’s information but also establishes a foundation of trust against growing Cyber threats.
The digital landscape is constantly evolving, and new security threats emerge regularly. In the unfortunate event of a security breach, VAs must know how to respond quickly and effectively to mitigate damage. This includes understanding the necessary steps, who to contact, and how to limit the impact on their Client’s privacy and security.
Ultimately, comprehensive training and awareness empower Virtual Assistants to effectively manage their Client’s online security and privacy. In the same way, staying compliant and preserving their reputation as security stewards are integral aspects of this role.
 With the rise of remote desktop access, Virtual Assistants have gained the ability to work seamlessly within digital environments. While this digital transformation provides several benefits, it also highlights significant issues related to online security and privacy.
With the rise of remote desktop access, Virtual Assistants have gained the ability to work seamlessly within digital environments. While this digital transformation provides several benefits, it also highlights significant issues related to online security and privacy.
Remote desktop access (RDA) is an important tool that significantly improves the capacities of a Virtual Assistant. This allows VAs not only to access their Clients’ systems remotely but also to handle data directly on the Client’s system. Additionally, RDA allows Clients to have controlled access and monitor VA activities in real-time, which promotes transparency and oversight. By keeping security measures and addressing technical problems quickly, RDA helps people work together smoothly while ensuring strong privacy protection.
However, by effectively putting it into action needs a careful mix of ease and safety. For this reason, both the Virtual Assistant and the Client must use strong encryption and handle data responsibly.
In essence, Remote Desktop Access is an indispensable tool that helps Virtual Assistants. Not only does it offer effective and secure but also privacy-conscious support within the complex world of today’s digital workspaces.
 By using third party tools allows Virtual Assistants to focus on their tasks while relying on proven solutions. These tools often provide features that help Companies in following these rules more conveniently. Subsequently, a well-rounded approach to managing security and privacy involves mixing reliable third party tools to spread out risks.
By using third party tools allows Virtual Assistants to focus on their tasks while relying on proven solutions. These tools often provide features that help Companies in following these rules more conveniently. Subsequently, a well-rounded approach to managing security and privacy involves mixing reliable third party tools to spread out risks.
It’s important to note that third party tools offer significant benefits, so choose them wisely. Both Virtual Assistants and Clients should carefully evaluate any possible help to ensure alignment with the company’s security and privacy requirements. Although third party tools are valuable, they should be used together with good Cybersecurity practices, training for employees, and a solid security plan overall. Hence, make sure these tools come from trusted Providers with a strong history in Cybersecurity.
Every click matters, especially as data breaches and cyber threats are more frequent. This emphasizes that having a capable Virtual Assistant is not just a convenience but a strategic imperative. They are your reliable allies who guarantee your online actions are safe and secure. By building a strong Partnership based on trust and assertive security measures, you can explore the digital world with confidence.
Want to offload your workload? Our Virtual Assistants are here to help with your tasks. Talk to us!